
 |
|
 |
|
Back to Article List Who Else is Using Your Wireless Network? By Laura Taylor March 25, 2004 Executive Summary Information Technology (IT) security industry experts continue to warn us that wireless networks have significant vulnerabilities. Taking precautions is a smart way to mitigate risks. Relevant Technologies tested Wireless Watch Home 2.0 (WWH) to evaluate its claim as an effective and affordable intrusion detection system (IDS) for home wireless networks. Background on Wireless Security Wireless networks are inherently insecure. If you haven't put in place security safeguards, anyone within 300 feet of your house can tap into your wireless access point and join your wireless network. Due to the default settings in both Microsoft operating systems and wireless routers, wireless networks are so easy to join that your neighbors might be using your wireless network (or you might be using theirs) and not even realize it. Cryptography Experts have lambasted wireless networks as being easy to exploit. While Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and Temporal Key Integrity Protocol (TKIP) all add layers of security to wireless networks, it is a well-established fact that cracking WEP encryption keys is not that hard to do. Most people who use computers at home, whether the computer is their own personal system, or a laptop owned by their company, don't go through the trouble to enable wireless security protocols. Many people using wireless networks don't even have a personal firewall installed on it. Using wireless networks without configuring security controls is risky and means your systems and data are susceptible to compromise by unauthorized users. Record Network Friends and Foes Relevant Technologies took Wireless Watch Home 2.0 (WWH) into our lab to see how well it performed as an IDS on home wireless networks. We downloaded WWH from OTO's Software's web site and found that it installed without incident. When it first starts up, it scans your network and returns a list of devices asking you to identify them as friends or foes. For each device that it finds, it presents you with the IP address and MAC address, as well as the manufacturer and probable type of device. With both addresses, you have enough information to determine a starting point from which to track down anyone who tries to use your Wireless Access Point (WAP). Access times are also recorded so that you can trace times of data corruption back to intrusion records. Once WWH is installed and running, it alerts you via pop-up window and flashing icon when any new device is detected on the network. This is WWH’s main function and it successfully performed this task throughout our testing. We tested WWH on both 802.11b and 802.11g equipment and found that it is compatible with either. OTO Software Corporate Information OTO Software 1880 Arapahoe Street, Suite 3205, Denver, CO 80202 Wireless Watch 2.0 www.otosoftware.com 888-212-1992 Figure 1: WWH alerts you when a new visitor is detected on your network 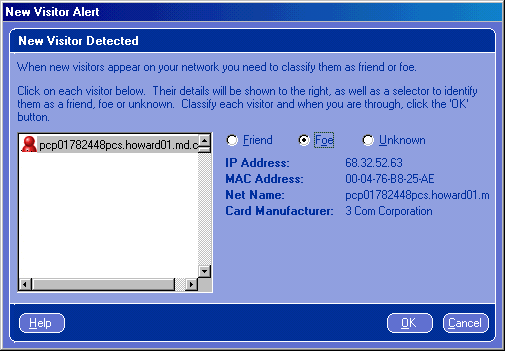 You can rename the PCs on your network with familiar names such as the various names of members of your family. You can also rename suspicious wireless network devices accordingly such as "unknowing neighbor" or "suspected hacker". Figure 2: Find out system information about your wireless network "guests" 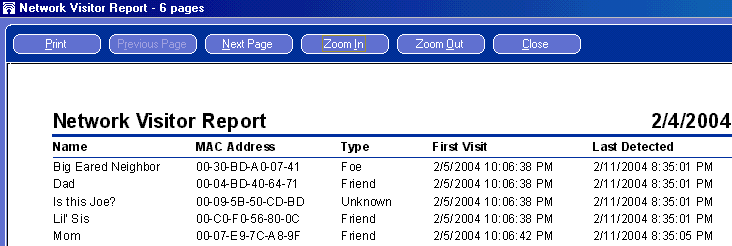 While Relevant Technologies does not advocate leaving your wireless network turned on when you're not physically present, if for some reason you need to do this, for example if you have a live data transfer running that you don't want to interrupt, Wireless Watch 2.0 can record who accesses your wireless network in your absence. If at some point in the future you notice that unauthorized access of your systems occurred while you were gone, you will have a recorded log file of everyone who was on your network during the period of suspicious activity. Using WWH in this manner requires that you leave it running on the unattended system that you would like to monitor. Figure 3: Record usage times of your suspected network foes 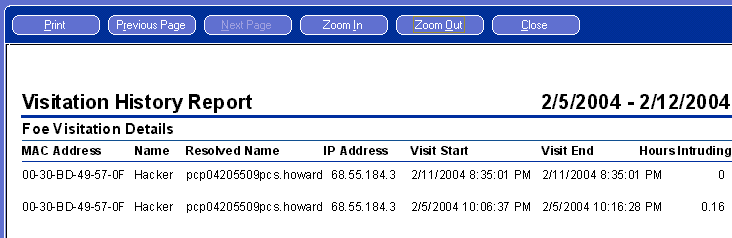 Other Uses for Wireless Watch Home 2.0 The product name, Wireless Watch 2.0, is somewhat misleading in that it suggests you can only view users on wireless networks. However, what we discovered is that you can actually use Wireless Watch to view your wired network guests as well. If you use a cable service, Wireless Watch tells who else is on your network segment. In reality, Wireless Watch is a personal intruder reporting system for any and all types of networks. One thing we especially liked about Wireless Watch 2.0 is that it enables you to see if your wireless card has inadvertently changed networks. Parents can easily track and record when their kids are accessing the network, even when Mom and Dad are still at work and the kids are home alone after school. However, technology savvy kids will find it easy to disable and turn off so if using it to monitor your kids, you'll need to not let them know which client system in the house is running the software. The downside of Wireless Watch is that hackers can also use it to see you and find out your system information. Though it is not marketed as a wireless scanner, it basically provides some of the same type of information that wireless scanners provide, in addition to its IDS functions. As long as hackers are looking at you, you might as well obtain the tools they use to look at them so you can track who might be performing reconnaissance on your system information for a potential future attack. Pricing and Usability Keep in mind that Wireless Watch 2.0 is a monitoring tool and it does not actively stop intruders. It is a surveillance camera for your network and if you want to record the network passersby, it seems to work well and is easy to use. No prior networking experience is required to be able to use it, although even experienced network users who enable router security features can find value in WWH due to its ability to detect an intruder who may have made it through the router security features. Wireless Watch is priced at $29.95 a license, which seems reasonable based on the awareness it provides. As of this writing, Relevant Technologies could not find any another products on the market in this price range with the same capabilities. Wireless Watch 2.0 works as advertised and offers significant network intrusion detection capabilities to both wireless and cable based networks. |
| Copyright 1997-2025 Relevant Technologies. All rights reserved | Legal and Privacy | Sitemap Email: info@relevanttechnologies.com | 8115 Maple Lawn Blvd, Suite 350, Fulton, MD 20759 |