
 |
|
 |
|
Back to Article List Find Application Security Holes with AppScan! By Laura Taylor May 3, 2007 Executive Summary Watchfire’s AppScan 7 (AppScan) is just the thing for detecting website vulnerabilities. Whether your organization is a financial institution, a managed service provider, or hosts its own web applications that contain confidential and private information, AppScan finds the holes. Specifically designed to find web based vulnerabilities, AppScan is suitable for use on both intranet and Internet based applications. I recently used AppScan on a consulting engagement and found it to be one of those products that anyone doing security audits shouldn’t be without. Let me tell you how it works, and what I liked best about it. What I Used AppScan For I used AppScan when performing a compliance audit on a large financial institution that uses a digital vault and web based transaction engine to process eMortgages. Online mortgages, a.k.a. eMortgages, are on the rise due to the fact that it saves both lenders and borrowers money. Applying for a mortgage online can save a buyer as much as $500.00. According to the Mortgage Electronic Registry System (MERS), there are almost 4,000 banks that are either processing online mortgages today, or are gearing up to do so soon. I used AppScan to find the vulnerabilities in an online eMortgage transaction engine. With web attacks on the rise, all financial institutions with web based applications should scan their applications regularly. The objective of the audit I performed was to look for security vulnerabilities of a web application, so it didn’t make sense to use a network scanner that looks for holes in operating systems and network configurations. That’s not to say that looking for vulnerabilities in operating systems and network configurations is not important. However, as of this writing, you can’t find very many application vulnerabilities using tools that were designed to find holes in networks and operating systems. It turns out that the financial institution’s online mortgage system was pretty tight and has few security vulnerabilities. Though even if that were not the case, the purpose of this article is not tell you about someone else’s security vulnerabilities. What I learned in the process of performing the audit is how much I liked AppScan, and how powerful a tool it is. I’m here to share with you some of the cool features of AppScan discovered during the process of using it. Ease of Use One of the things I liked best about AppScan was how easy it was to use. AppScan took about an hour to install and configure, though that timeframe included the time it took to download the software, unbundle it, extract files, and install the license. The installation went without a hitch, and I installed the whole thing without having to open the manual or call the support line. The AppScan User Guide comes bundled with the software and includes 242 pages of detailed information that includes screenshots and searchable text. Though the documentation is well written, it will certainly help if the person using AppScan has an information security background. Though it is easy to use, it is also a sophisticated application with powerful features that can be best understood by someone who is familiar with the different types of attacks that web applications are vulnerable to. Once vulnerabilities are detected, a dashboard view ranks them from high to low severity as illustrated in Figure 1. Double clicking on the vulnerability expands it to show the URL that hosts the problematic code. If you then click on the Request/Response tab, the buggy code is highlighted as illustrated in Figure 2. The point and click scan dashboard can organize vulnerabilities by severity, by name, or by how pervasive they are. Reporting Features One of the features of AppScan that I particularly like are its reporting features. AppScan has the ability to generate numerous different types of reports including compliance and industry standard/best practice reports. Consultants that have numerous customers that are trying to comply with different compliance laws will especially like the compliance reports. The different compliance laws that AppScan can generate 38 compliance reports for including (but not limited to):
Along side of the Request/Response tab are tabs that provide all the data you would need to have a developer to fix the vulnerability in the code. There are fix recommendations and general advisories related to the vulnerabilities found. You can also recreate how a cyber criminal would exploit the vulnerability by clicking on 'Show in Browser'. The reporting features include CVE references so that you can find out more information on vulnerabilities reported using MITRE’s CVE naming standard for vulnerabilities. Figure 1. A small section (cropped image) of the reporting interface 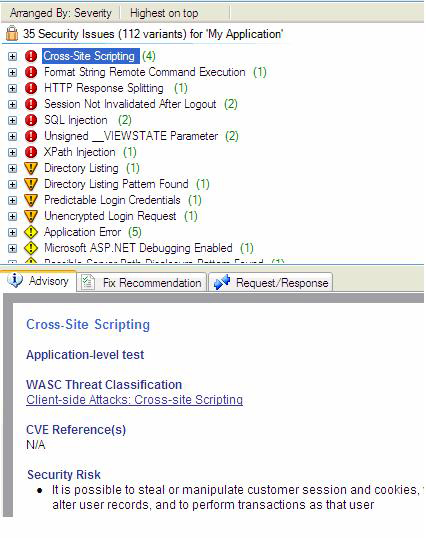 For developers, AppScan has a unique capability that allows you to move from a Security Issues view to a Remediation Tasks view. The former view is for the person responsible for uncovering the vulnerabilities. However, with a single mouse click the latter provides a straightforward list of security development tasks. It appears to be a very effective way to help developers focus on specific coding issues versus having to decipher security vulnerabilities - something that is a challenge if a developer does not have a security background. See Figure 2. Figure 2. The problematic code is highlighted 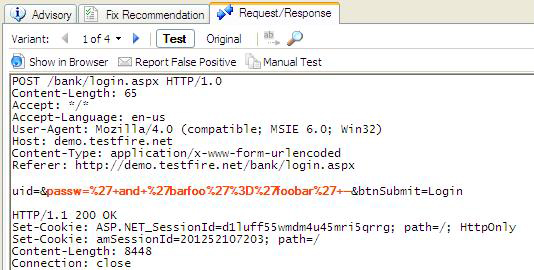 The Token Analyzer The Token Analyzer is a feature that enables you to determine the strength (and weaknesses) of session tokens. The reason that you may be interested in finding out weaknesses in your session tokens is to prevent man-in-the-middle attacks and session hi-jacking. The Token Analyzer can analyze the randomness of your session ID which will give you an idea of how vulnerable your sessions are to attack. The more random your session IDs are, the less vulnerable your sessions are to session hi-jacking. The token analyzer tests help you understand if your application is using weak token algorithms by performing the following token analysis tests:
If a session is stolen, cyber criminals can potentially find out UserIDs, passwords, and gain direct access to confidential and private information. If, for example, your financial institution is using weak session IDs, a cyber criminal could potentially gain access to your online banking account and transfer all of your money out of your account. Figure 3. Token Analyzer The token analyzer is one of the most unique features of AppScan. Right now though, the only way to include token analyzer results into a report is to take screenshots of the graphs and paste them in and put in and developer your own commentary and recommendations. According to Watchfire, they are working on integrating the token analyzer scan results into the main reporting wizard. Role-Based Access Controls (RBAC) Provides Nice Separation of Duties If you want to share the scan results across your organization, the reporting component enables you do that by giving different people login accounts to the web based results repository. For example, the CIO or CISO, as well as the security engineers and application developers, may all be interested in viewing the same results from different locations. Different permissions can be assigned to different user roles enabling some users to view results, and others to perform scans as well. By supporting Role-Based Access Controls (RBAC), AppScan enables organizations to ensure a separation of duties exists between the people viewing the reports, and the people generating the reports. Though the following reason may not fly with helping justify the purchase of AppScan, one reason I liked AppScan was simply because it was fun to use. There are so many different features that I definitely didn’t have time to try them all. However, all of the features that I did try worked as advertised. How AppScan Minimizes False Positives AppScan finds vulnerabilities by interacting with applications the way a user (or an intruder) would. It feeds in different input variables to the applications, the same way a user or intruder might do. For example, in order to expose a SQL Injection vulnerability, AppScan will append a host of string variants to an original parameter value. A detailed Test Policy Manager allows the user to see all the code mutations that AppScan is performing in order to identify vulnerabilities as illustrated in Figure 4. Because AppScan feeds in variables the way a user would, if vulnerabilities are discovered, they are for the most part always real, and with AppScan you will see few false positives. Figure 4. AppScan reduces false positives by using real string variants AppScan can find vulnerabilities that can be exploited by the following types of attacks (this list is not exhaustive):
AppScan is the ideal tool for:
Other Considerations While AppScan is a great tool for uncovering application vulnerabilities, if you want to uncover operating system level vulnerabilities you’ll need to also use a network infrastructure scanner like the Qualys QualysGuard scanner or IBM’s Internet Security Scanner. Whether you use AppScan or some other application scanner, you should scan your applications and websites regularly. There is a multitude of information that cannot be verified by using a scanner of any sort and a scanner should not be your only means of determining risks to enterprise networks. For example, a scanner will not be able to determine if your end-user Rules of Behavior is adequate. A scanner will also not be able to determine if your organization has a well-thought out patch testing process, or a well-thought out change control or configuration management process. Scanners are good for testing technical controls, but are not well suited for testing management controls, and certain operational controls. A scanner can’t tell you if a data center is manned 24 x 7 and cannot verify if there are two-factor authentication badge readers at the doors that require PINs. A scanner cannot tell you if your organization has a well though-out user recertification process or if your contingency plan will work. As of today, there are numerous security tasks that cannot be replaced by human thought. Future Predictions Related to AppScan and Watchfire It would be nice if there were one scanner you could scan everything with – applications and the underlying systems and networks. I expect that in the future, the technology for application scanners, and scanners for systems and networks, will converge. Today, corporate consumers have to license two different types of scanners if they want to ascertain vulnerabilities for both applications, and systems and networks. Aside from keeping the initial procurement cost high, licensing two different products drives up the Total Cost of Ownership for end-users by creating two products to install and support, two products to train staff for, and two scans that have to be run. As the trend toward market consolidation grows, Relevant Technologies anticipates that application scanners will merge with network/system scanners to eventually provide one-stop-shopping for security scanners. Typically pure-play companies (companies that do one thing well) are prime acquisition targets. For that reason, Relevant Technologies finds Watchfire to be ripe for acquisition. While Relevant Technologies has no knowledge of any acquisition discussions at this time, the information security market leaders have long and storied histories of acquiring smaller innovative pure-plays. Companies that may want to acquire Watchfire would likely include larger companies that are working on building out their portfolio of security products and services such as: Symantec, McAfee, Computer Associates, IBM, Cisco, or EMC. Since compliance regulations are driving the information security market, and Watchfire’s reporting features hone in on numerous compliance laws and regulations, Watchfire is well-positioned to negotiate. Seal of Assurance  Relevant Technologies has assigned its Seal of Assurance to Watchfire’s AppScan. Our Seal of Assurance is assigned to products that work as advertised, and offer innovation, quality, and usefulness. More information on our Seal of Assurance program can be found by clicking here. Relevant Technologies has assigned its Seal of Assurance to Watchfire’s AppScan. Our Seal of Assurance is assigned to products that work as advertised, and offer innovation, quality, and usefulness. More information on our Seal of Assurance program can be found by clicking here.
|
| Copyright 1997-2025 Relevant Technologies. All rights reserved | Legal and Privacy | Sitemap Email: info@relevanttechnologies.com | 8115 Maple Lawn Blvd, Suite 350, Fulton, MD 20759 |