
 |
|
 |
|
Back to Article List Securing an Exchange Server by Limiting Mail Relay Use By Brien M. Posey December 8, 2003 One of the most important steps that you should take in securing an Exchange Server is to either disable or restrict the use of mail relay. In case you arenít familiar with mail relay, it refers to the practice of passing a message through a server and rerouting it to its final destination. While there are some legitimate uses of the mail relay feature, mail relay tends to be heavily abused by spammers. Many spammers actually use a program that searches the Internet for mail servers with the mail relay feature enabled. Once a spammer finds such a server, they begin to route SPAM through the server. There are several reasons why spammers do this. The main reason though is that passing SPAM through your server helps to conceal the spammerís identity. Keep in mind that many of the currently available anti SPAM software packages contain black lists of known spammers. If a spammer has been blacklisted, or just wants to keep themselves from being blacklisted, they need to obscure their identity, and exploiting mail relays provides the perfect solution. The problem is that if a spammer does relay mail through your mail server then the resulting SPAM appears to have come from you. While the SPAM may not bear your personal E-mail address, it will use your domain name or your mail serverís IP address. Once a stream of SPAM starts coming from your mail server, itís only a matter of time before one of the anti SPAM organizations black lists your domain which you'll probably agree is a pretty serious matter.. There are a few different companies that compile black lists. These black lists are then relied upon by almost all of the major anti SPAM products. Therefore, once your domain has been black listed, no one in your organization will be able to send E-mail to anyone using an anti SPAM product that makes use of the various black list databases. Once your domain has been blacklisted, it can be quite an ordeal to be taken off of the list. Even if you arenít concerned about being black listed, there are other negative consequences to being used as a mail relay by spammers. Spammers could channel millions of messages through your server each day. This robs your organization of Internet bandwidth. It also consumes server resources such as disk space, memory, and CPU time. In fact, there have been documented cases in which hackers have launched a denial of service attack against a mail server by relaying millions of messages through it. In this case, the server gets so bogged down that it canít process legitimate mail. As I said earlier though, mail relay can be used for legitimate purposes too. For example, suppose that a business uses one company to act as an ISP and to host their Web site. Now suppose that this company were to relocate to another state. They would have to get a new ISP, but may choose to keep their current hosting company. Because the company has switched ISPs, the company is no longer authenticating directly into the hosting companyís domain. Therefore, if employees at the company want to retrieve E-mail from the hosting companyís Exchange Servers, then they will have to use an alternate type of authentication. They may also find that they have to use an SMTP / POP3 client rather than an Exchange client for the purposes of accessing E-mail. In essence, the employees are using the SMTP / POP3 mail client to relay mail through the hosting companyís Exchange server. Obviously, there is nothing malicious about this activity. This is just an example of a legitimate mail relay situation. As you can see, there are situations where mail relay can be implemented legitimately. Exchange Server even allows you to control who can and canít relay mail. If you donít have a need for mail relay though, itís best to disable the mail relay feature completely. In Exchange 2003, you can disable or restrict mail relay by using the Exchange System Manager. To do so, open the System Manager and navigate through the console tree to Administrative Groups | your administrative group | Servers | your server | Protocols| SMTP | Default SMTP Virtual Server, as shown in Figure A. Figure A: Navigate to the Default SMTP Virtual Server 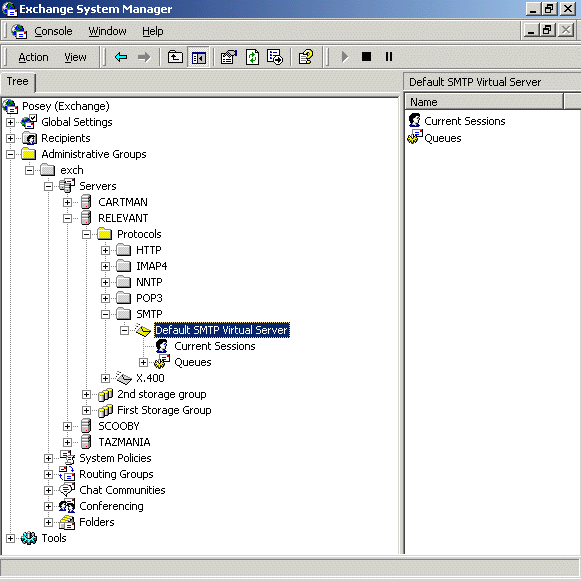 Now, right click on the Default SMTP Virtual Server and select the Properties command from the resulting shortcut menu. When you do, Exchange will display the Default SMTP Server Properties sheet. Next, select the Access tab, as shown in Figure B. Figure B: Mail relay is controlled through the Access tab of the Default SMTP Virtual Server Properties sheet. 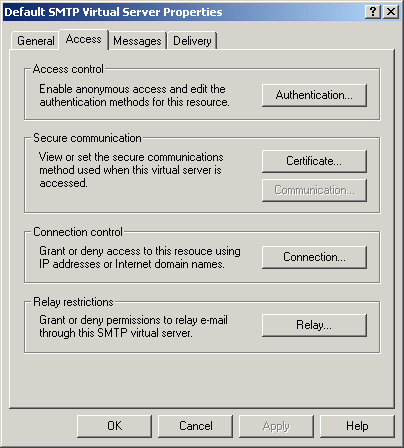 At this point, click the Relay button and you will see the Relay Restrictions screen, shown in Figure C. You can set Exchange to allow everyone except for those listed to relay mail, or you can block mail relay to everyone except for those listed. Itís best to block mail relay to everyone except for those listed. There is also a check box that you can use which will allow anyone who is authenticated into your network to relay mail regardless of whether or not they would otherwise be allowed to do so. Whether or not this check box should be selected depends on your organizationís own security policy. If you choose to allow certain individuals to relay mail., you can specify those allowed to relay mail by either entering their IP address or by entering their domain. Itís much better to enter an IP address than a domain name. Entering a domain name causes Exchange to have to perform DNS queries every time someone tries to relay a message and often places a huge burden on the processor. Furthermore, specifying a domain allows anyone from that domain to relay mail, whereas an IP address is specific to an individual computer. Furthermore, it is much too easy for someone to figure out what domains are allowed to relay mail and then spoof the domain name as a way of getting around your relay restrictions. Figure C: The Relay Restrictions dialog box allows you to control who, if anyone, is allowed to relay mail through your server. 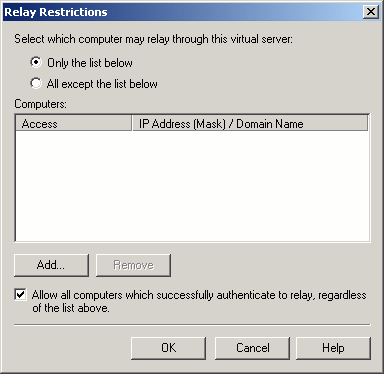 Although disabling or restricting mail relay is a good start, you will also want to try to relay mail through your server to see if your serverís configuration is actually preventing mail relays. The testing process is done from the command prompt of a PC thatís connected to the Internet. The test PC must be outside of your organization in order for the test results to be accurate. Begin by opening a Command Prompt Window and entering the command: TELNET mail.server.com 25, as shown in Figure D. Figure D: Begin by telneting to your server through port 25. 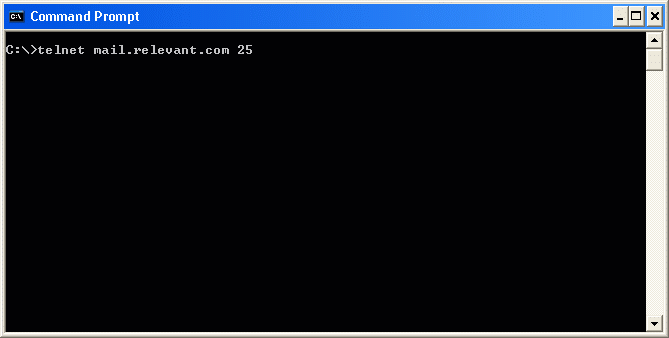 In this command, mail.server.com should be replaced by the actual server name. For example, if I wanted to test my mail server, Iíd enter mail.relevant.com in place of mail.server.com. Upon entering this command, the telnet session should respond by saying that it is trying the serverís IP address. To be more correct though, the telnet session is trying to communicate with the server at the listed IP address through port TCP port 25. You then may or may not see a message stating that the Escape character is Ď^]? Whether or not you see the message depends on the version of Exchange that you are connecting to and how fast the connection is. Sometimes this message flashes too quickly to see. At any rate, this message is unimportant. At this point, the screen will clear and you will see a message that says something like 220 snr-nts-mail02.server.com ESMTP Server (Microsoft Exchange Internet Mail Server 5.5.2653.13) ready You can see an example of this in Figure E. Figure E: The Telnet session will give you a ready status once the connection has been confirmed. 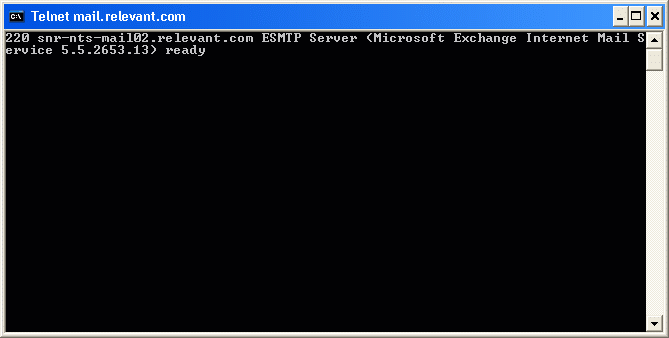 Again, the actual message may vary depending on the version of the Exchange server that you are connecting too. The message might be as simple as 220 mail.server.com. It isnít really important what this message says as long as it starts with a 220 and it identifies the server that you are connecting to. Such a message means that you are attached to the target server. Keep in mind though that so far we have only attached to the server, we havenít actually relayed a message through it yet. Now that a connection is established, we need to tell the server that we want it to send a message on our behalf. This is done through the HELO command. Simply enter HELO mail.server. For example, in our case, we would enter HELO mail.relevant. After entering the command, the server should reply with a message that says 250 OK. You can see an example of this shown in Figure F. Figure F: The HELO command is used as the first step in the mail relay sequence. 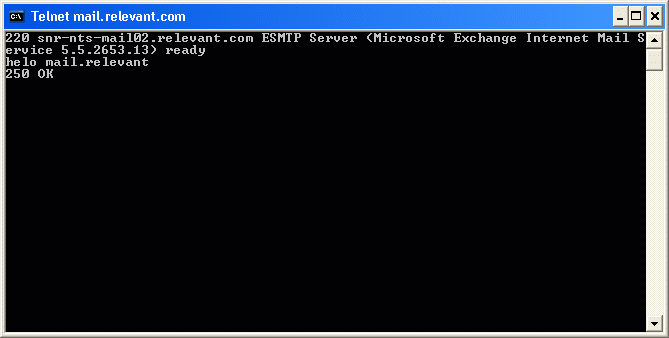 Mens Indianapolis Colts Pro Line Charcoal Lightweight Full Zip Hooded Jacket,Denver Broncos 14" Nutcracker,Men's New York Jets Black First Down Boardshorts Patriots Jerseys On Sale.Girls Youth Green Bay Packers Clay Matthews Green Fade Route Name & Number T-Shirt,Green Bay Packers Green 12oz. Neoprene Bottle Cooler,Men's Seattle Seahawks Jimmy Graham Nike College Navy Game Jersey.Men's Philadelphia Eagles Cutter & Buck Black Mason Full-Zip WeatherTec Jacket,Men's Buffalo Bills New Era Royal Tech Grade 39THIRTY Flex Hat Patriots Jerseys Cheap.Men's Dallas Cowboys Michael Irvin Nike White Retired Player Limited Jersey,Kansas City Chiefs Replica Football Ornament Cheap New England Patriots Jerseys.Youth Dallas Cowboys Charcoal Fleece 1/2-Zip Jacket,Women's Chicago Bears Levi's Orange 49ers Barstow Western Long Sleeve Button-Up Shirt.Antigua Minnesota Vikings Viper Full Zip Jacket - Purple,Men's Minnesota Vikings Concepts Sport Camo Boxer Shorts,Oakland Raiders Chrome Can Tumbler.Men's Kansas City Chiefs Derrick Johnson Nike Red Team Color Limited Jersey,New York Giants Armor Band Phone Case Patriots Jerseys Wholesale.Infant Seattle Seahawks College Navy/White 2-Pack Game Day Long Sleeve Bodysuit Set,New England Patriots Galaxy S6 Dual Hybrid Case
Now, we need to specify the sender of the message. Remember that we want to simulate someone from outside your organization trying to relay mail through your network. Therefore, when you specify the sender of the message, you should make up a fake domain name or at the very least use something that doesnít exist on your network. For testing purposes, I will be using USER1@domain1.com as the sender.To specify the sender, enter the command MAIL FROM: sender@domain.com. In this particular case, since I am using USER1@domain1.com as the sender, I would enter MAIL FROM:USER1@DOMAIN1.COM. Upon entering this command, the telnet session should generate a message that says 250 OK ?MAIL FROM USER1@DOMAIN1.COM. You can see an example of this in Figure G. Figure G: Use the MAIL FROM command to specify the sender. 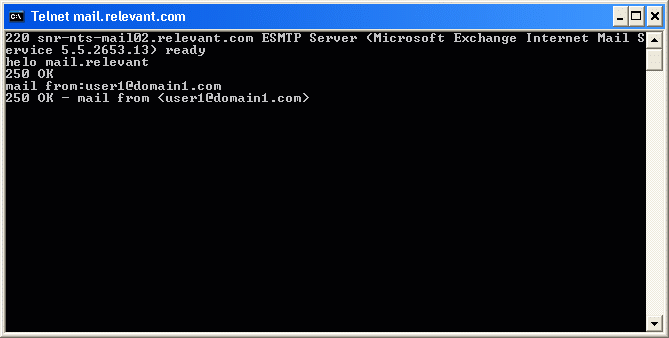 Now, you must specify the recipient of the message. Again, you will want to use a domain that doesnít exist on your network. For testing purposes I will be using the E-mail address USER2@domain2.com. The syntax for the recipient command is RCPT TO:recipient@outsideaddress.com. Of course you would substitute recipient@outsideaddress.com with the actual address. In this case the actual command would be RCPT To:USER2@DOMAIN2.COM. When you press Enter you will find out if your server is relaying mail or not. If relaying is blocked, you will receive a message that says 550 RELAYING IS PROHIBITED. You can see an example of this shown in Figure H. Figure H: You should get a message stating that relay is prohibited. 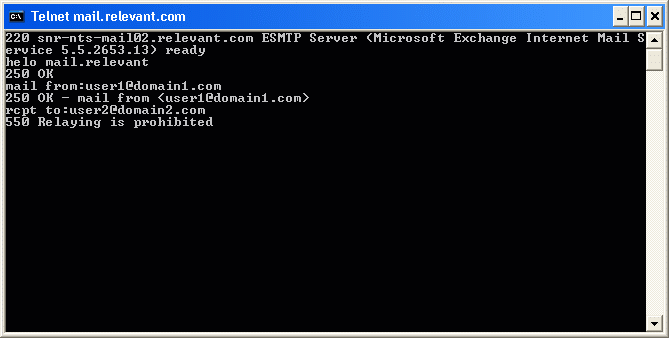 As long as you receive the Relay is Prohibited message, then the restrictions that you have placed on the server are working correctly. Keep in mind though that the relay restrictions are implemented at the SMTP virtual server level within Exchange. This means that the restrictions must be imposed on each individual server. Simply securing one server does not secure the entire Exchange organization. Furthermore, if you have multiple SMTP virtual servers on a single Exchange Server, then each SMTP virtual server must be secured individually. Remember, disabling or limiting mail relay is absolutely essential to your Exchange Organizationís well being. Taking a little time to disable and youíre your Exchange serverís mail relay feature will keep you off of the SPAM black list and will keep the spammers from using your server to spread SPAM. |
| Copyright 1997-2025 Relevant Technologies. All rights reserved | Legal and Privacy | Sitemap Email: info@relevanttechnologies.com | 8115 Maple Lawn Blvd, Suite 350, Fulton, MD 20759 |